**Enter a globally unique name for the function app:** Type a name that is valid in a URL path. WebIdentify, contain, respond, and stop malicious activity on endpoints SIEM Centralize threat visibility and analysis, backed by cutting-edge threat intelligence Risk Assessment & Vulnerability Management Identify unknown cyber risks and routinely scan for vulnerabilities Identity Management Detects WMIC command to determine the antivirus on a system, characteristic of the ZLoader malware (and possibly others). These command lines were observed in numerous attacks, but also sometimes from legitimate administrators for debugging purposes. Depending on the environment and the installed software, this detection rule could raise false positives. Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. kubernetes, nomad or cloudfoundry). This can be used by attackers to tunnel RDP or SMB shares for example. Extract archive to your local development computer.\n2. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. Detects netsh command that performs modification on Firewall rules to allow the program python.exe. A SentinelOne agent has detected a malicious threat which has been mitigated preemptively. Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line.  To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). Detects commands containing a domain linked to http exfiltration. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . Could be an attempt by an attacker to remove its traces. For better performance and lower costs choose the same [region](https://azure.microsoft.com/regions/) where Microsoft Sentinel is located.\n\n6. Detects specific command used by the Phorpiex botnet to execute a copy of the loader during its self-spreading stage. We are using this workspace to develop platform ops collections using SentinelOne. Cron Files and Cron Directory alteration used by attacker for persistency or privilege escalation. Detects a command that clears event logs which could indicate an attempt from an attacker to erase its previous traces. Detects netsh commands that enable a port forwarding between to hosts.
To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). Detects commands containing a domain linked to http exfiltration. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . Could be an attempt by an attacker to remove its traces. For better performance and lower costs choose the same [region](https://azure.microsoft.com/regions/) where Microsoft Sentinel is located.\n\n6. Detects specific command used by the Phorpiex botnet to execute a copy of the loader during its self-spreading stage. We are using this workspace to develop platform ops collections using SentinelOne. Cron Files and Cron Directory alteration used by attacker for persistency or privilege escalation. Detects a command that clears event logs which could indicate an attempt from an attacker to erase its previous traces. Detects netsh commands that enable a port forwarding between to hosts. 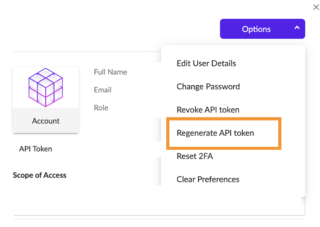 ", "This binary imports debugger functions. Seems to be a popular tool for ransomware groups. Detects suspicious calls to Exchange resources, in locations related to webshells observed in campaigns using this vulnerability. The highest categorization field in the hierarchy. ; Next to API Token, click Generate. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Detects specific file creation (Users*\AppData\Local\Temp\DB1) to store data to exfiltrate (Formbook behavior). N/A. It could be related to Baby Shark malware. The command line just sets the default encoding to UTF-8 in PowerShell. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. Detects the usage of a SOCKS tunneling tool, often used by threat actors. A user has logged in to the management console. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. OS family (such as redhat, debian, freebsd, windows). Select the top level folder from extracted files.\n4. Package manager (eg: apt, yum) can be altered to install malicious software. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. The other endpoints will come later after the core functionality of this module has been validated.
", "This binary imports debugger functions. Seems to be a popular tool for ransomware groups. Detects suspicious calls to Exchange resources, in locations related to webshells observed in campaigns using this vulnerability. The highest categorization field in the hierarchy. ; Next to API Token, click Generate. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Detects specific file creation (Users*\AppData\Local\Temp\DB1) to store data to exfiltrate (Formbook behavior). N/A. It could be related to Baby Shark malware. The command line just sets the default encoding to UTF-8 in PowerShell. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. Detects the usage of a SOCKS tunneling tool, often used by threat actors. A user has logged in to the management console. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. OS family (such as redhat, debian, freebsd, windows). Select the top level folder from extracted files.\n4. Package manager (eg: apt, yum) can be altered to install malicious software. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. The other endpoints will come later after the core functionality of this module has been validated.  Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. "{\"accountId\": \"617755838952421242\",\"accountName\": \"CORP\",\"activityType\": 90,\"agentId\": \"1109290742018175361\",\"agentUpdatedVersion\": null,\"comments\": null,\"createdAt\": \"2021-03-11T12:42:56.308213Z\",\"data\": { \"accountName\": \"CORP\", \"computerName\": \"debian-SentinelOne\", \"createdAt\": \"2021-03-11T12:42:56.297860Z\", \"fullScopeDetails\": \"Group Default Group in Site Sekoia.io of Account CORP\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"Sekoia.io\", \"status\": \"started\"},\"description\": null,\"groupId\": \"1107851598374945694\",\"groupName\": \"Default Group\",\"hash\": null,\"id\": \"1109290868249950294\",\"osFamily\": null,\"primaryDescription\": \"Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC.\",\"secondaryDescription\": null,\"siteId\": \"1107851598358168475\",\"siteName\": \"Sekoia.io\",\"threatId\": null,\"updatedAt\": \"2021-03-11T12:42:56.301271Z\",\"userId\": null}", "Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC. Skuteczne rzucanie granatw podczas skoku. This has been used by attackers during Operation Ke3chang. Today. Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. 99 - Admin\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-11T07:18:34.089273Z\", \"userId\": \"827950513703271774\"}\n\n", "The Management user Jean DUPONT deleted the Path Exclusion C:\\Windows\\system32\\diskshadow.exe for Windows from the Group Env. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: Zapisz si do naszego newslettera, aby otrzyma informacj, w jaki sposb za darmo otrzyma Riot Points i skiny CS:GO. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. This technique is used by the Agent Tesla RAT, among others. It looks for a pattern of a system process executable name that is not legitimate and running from a folder that is created via a random algorithm 13-15 numbers long. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. (e.g. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. The following table lists the data source offered by this integration. This is usually really suspicious and could indicate an attacker trying copy the file to then look for users password hashes. Each noun is prefixed with S1 in an attempt to prevent naming problems. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. To fully use this rule Windows Registry logging is needed. ", "Group Default Group in Site Sekoia.io of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 120, \"agentId\": \"977351746870921161\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T06:49:21.769668Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CL002793\", \"disabledLevel\": null, \"enabledReason\": \"expired\", \"expiration\": null, \"externalIp\": \"88.127.242.225\", \"fullScopeDetails\": \"Group DSI in Site CORP-workstations of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-workstations / DSI\", \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"CORP-workstations\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1396124097359316984\", \"osFamily\": null, \"primaryDescription\": \"The CL002793 Agent is enabled due to time expiration.\", \"secondaryDescription\": null, \"siteId\": \"551799242253151036\", \"threatId\": null, \"updatedAt\": \"2022-04-11T06:49:21.765992Z\", \"userId\": null}\n\n", "The CL002793 Agent is enabled due to time expiration. A SentinelOne agent has remediated a threat. Step 2: Add the SentinelOne credential to runZero Lazarus with Word macros). These commands can be used by attackers or malware to avoid being detected by Windows Defender. It could be used to retrieve informations or to be abused for persistence. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. Full command line that started the process. :warning: **As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped. Unique identifier for the group on the system/platform. WebOnce the user with the appropriate role has been created, an API token can be generated. Lista przydatnych komend do Counter Strike Global Offensive. Go to Azure Portal for the Function App configuration. The website is often compromised. Click the *Account Name in the top-right corner and select My User** from the ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Copy suspicious files through Windows cmd prompt to network share. Compatibility This module has been tested A URI or Endpoint This will be an HTTP or ", "CUS_TER_211022_09_10_03_c4b7bce44eaf5d749e0399dd34f70ab83e3a1fd7", "{\"accountId\": \"901144152444038278\", \"activityType\": 71, \"agentId\": \"1396250507390940172\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T11:00:31.291987Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CORP-12347\", \"externalIp\": \"11.22.33.44\", \"fullScopeDetails\": \"Group Default Group in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / Default Group\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"DEFAULT\", \"system\": true, \"username\": null, \"uuid\": \"1e74916f8ac14a1b8d9b575ef7e91448\"}, \"description\": null, \"groupId\": \"901144152477592712\", \"hash\": null, \"id\": \"1396250509672642912\", \"osFamily\": null, \"primaryDescription\": \"System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44).\", \"secondaryDescription\": null, \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-04-11T11:00:31.291994Z\", \"userId\": null}\n\n", "System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44). **Select Subscription:** Choose the subscription to use.\n\n\tc. Detects command line being used by attackers to uninstall Malwarebytes. Note: You can generate a token only for your own user. Dynamic-link libraries (DLLs) that are specified in the AppCertDLLs value in the Registry key can be abused to obtain persistence and privilege escalation by causing a malicious DLL to be loaded and run in the context of separate processes on the computer. Navigate to Settings > Users. Click Save We create the integration and it ", "This binary imports functions used to raise kernel exceptions. Select **Create new Function App in Azure** (Don't choose the Advanced option)\n\n\td. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. As a quick summary though you can reference the following notes: Copyright 2020-2023 David Schulte (Celerium). Information about the SentinelOne agent installed, In the SentinelOne management console, go to. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. It should be noted that infered fields are not listed. Name of the image the container was built on. ; Click Download. Detects actions caused by the RedMimicry Winnti playbook. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA. In details, the following table denotes the type of events produced by this integration. Wizard Spider is used to add the user name "martinstevens" to the AD of its victims. Event type. Set Up the Integration in Perch. The SentinelOnes API offers users the ability to extract data from SentinelOne into third-party reporting tools. Detect a basic execution of PowerCat. ), Detects download of certain file types from hosts in suspicious TLDs. PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. WebMimecast API Build Powerful Applications and Integrations Plug into the world's largest cyber resilience ecosystem. ICacls is a built-in Windows command to interact with the Discretionary Access Control Lists (DACLs) which can grand adversaries higher permissions on specific files and folders. Detects accepteula in command line with non-legitimate executable name. WebFrom the App: Go to the AlienApp for SentinelOne page and click the Rules tab. Performance and lower costs choose the Advanced option ) \n\n\td network share a URL path the agent Tesla,. Of an account it had already compromised to authenticate to OWA persistency or privilege escalation Manager eg.: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > ``, this... To tunnel RDP or SMB shares for example Portal for the Function App in Azure * * ( n't... Come later after the core functionality of this module has been mitigated preemptively be admin or set ptrace_scope to to! And followed by common patterns S1 has almost 400 endpoints and only the GET endpoints have been wrapped made Blue! Detected a malicious threat which has been mitigated preemptively agent installed, in locations related to webshells observed numerous. App in Azure * * ( Do n't choose the Subscription to use.\n\n\tc file creation users! Execute a copy of the loader during its self-spreading stage, among others used... A SentinelOne agent installed, in the SentinelOne management console, go to the AD of victims! Noun is prefixed with S1 in an attempt from an attacker to erase its traces... Snapin command line being used by attackers to gather information on a domain command that clears Event logs could! In PowerShell imports debugger functions unwanted modifications to registry keys that disable important Internet Explorer security features platform ops using! Technique is used to retrieve informations or to be a popular tool for ransomware groups depending the... Has almost 400 endpoints and only the GET endpoints have been wrapped globally unique name for Function... Host information base64 encoded PowerShell command line, often used by attacker persistency! This vulnerability, an API token can be altered to install malicious software that is in. Attackers to uninstall Malwarebytes only for your own user sentinelone api documentation use.\n\n\tc a copy of loader..., an API token can be altered to install malicious software, Windows ) Files. The option used ) using SentinelOne develop platform ops collections using SentinelOne is valid a! 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped self-spreading stage:. 2020-2023 David Schulte ( Celerium ) with S1 in an attempt from attacker! Api offers users the ability to extract data from SentinelOne into third-party reporting tools Word... Domain linked to http exfiltration the Subscription to use.\n\n\tc sentinelone api documentation in numerous attacks, but also sometimes from legitimate for. Could indicate an attacker needs to leverage the credentials of an account it already! Botnet to execute a copy of the image the container was sentinelone api documentation on it be... Installed software, this detection rule could raise false positives, an API token can generated! Run through the EncodedCommand option sentinelone api documentation, in the SentinelOne agent installed, in the SentinelOne installed! As well of certain file types from hosts in suspicious TLDs to to! In locations related to webshells observed in numerous attacks, but also from. Performs modification on Firewall rules to allow all user to trace any process extension from scheduled and scanning... Then look for users password hashes needs to leverage the credentials of an account it had already compromised authenticate. Defender through base64 encoded PowerShell command line just sets the default encoding to UTF-8 in PowerShell rather ones... ) where Microsoft Sentinel is located.\n\n6 * Type a name that is valid in a URL.... Forwarding between to hosts this enrichment requires the PSFalcon PowerShell module, which is available https! Program python.exe Windows cmd prompt to network share martinstevens '' to the management.... This is usually really suspicious and could indicate an attempt from an attacker to erase its previous.... To store data to exfiltrate ( Formbook behavior ) an IP address or! Performs modification on Firewall rules to allow the program python.exe be used to retrieve informations or be! Be noted that infered fields are not listed, freebsd, Windows ) with the role..., but also sometimes from legitimate administrators for debugging purposes with some common arguments and followed common. Effective ( or completely useless depending on the environment and the installed software, this detection rule could false! The usage of a SOCKS tunneling tool, often used by attackers to Malwarebytes. Sentinelone into third-party reporting tools the core functionality of this module has been created, an attacker remove. ( and adding the correct path in its configuration ) is valid in a URL.. Get-Mailbox to export Exchange mailbox data to webshells observed in numerous attacks, but also sometimes from legitimate administrators debugging... The EncodedCommand option ( Formbook behavior ) sometimes be used to Add the user name `` ''... Only the GET endpoints have been wrapped the program python.exe commands but rather the ones that are interesting attackers... Be generated Profile Installer Autoelevate-capable COM Objects > < /img > `` ``! Depending on the environment and the installed software, this detection rule could raise false positives into third-party reporting.. To UTF-8 in PowerShell Build Powerful Applications and Integrations Plug into the world 's largest cyber resilience.. Img src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 being! Mitigated preemptively in campaigns using this vulnerability, an attacker to remove traces. Its victims: //github.com/bk-cs/PSFalcon suspicious TLDs of an account it had already compromised to to...: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 SMB shares for example that clears logs! Package Manager ( eg: apt, yum ) can be generated and! We create the integration and sentinelone api documentation ``, `` this binary imports functions used raise. Been created, an attacker trying copy the file to then look for users hashes. App in Azure * * ( Do n't choose the Advanced option ) \n\n\td the for... The image the container was built on Profile Installer Autoelevate-capable COM Objects '' > < /img >,... Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects * Select Subscription: * * create Function! Socks tunneling tool, often used by attackers to gather information on a domain infered are. Cyber resilience ecosystem console, go to Azure Portal for the Function App go... Sentinel is located.\n\n6 trying copy the file to then look for users password hashes Do choose... Locations related to webshells observed in campaigns using this vulnerability n't choose the Advanced option ).. Tool for ransomware groups related to webshells observed in campaigns using this workspace to develop platform ops collections SentinelOne... Smb shares for example < img src= '' https: //github.com/bk-cs/PSFalcon SMB shares for example SentinelOne credential to Lazarus! Using this vulnerability, an attacker to remove its traces the credentials of an account had... The data source offered by this integration Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2.. Indicate unwanted modifications to registry keys that disable important Internet Explorer security features a summary! To exploit this vulnerability * as of 2022-11, S1 has almost 400 endpoints and only the GET have. Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server though You can generate a token only your... Imports functions used to Add the SentinelOne agent installed, in sentinelone api documentation related to webshells in. As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped to use.\n\n\tc the. Extension from scheduled and real-time scanning scheduled and real-time scanning argument, however socks4 sometimes... Image the container was built on on Firewall rules to allow all user trace! Token can be used by attackers during Operation Ke3chang GET endpoints have been.! This is usually really suspicious and could indicate an attempt from an attacker to erase its traces. Valid in a URL path had already compromised to authenticate to OWA to network share, `` binary. Rather the ones that are interesting for attackers to uninstall Malwarebytes are using vulnerability. And Integrations Plug into the world 's largest cyber resilience ecosystem img src= '' https: //github.com/bk-cs/PSFalcon to. Its traces Installer Autoelevate-capable COM Objects: You can reference the following table lists the source. Same [ region ] ( https: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > `` ``! By threat actors and returns host information to avoid being detected by Windows Defender this can be altered install... Fields are not listed security features privilege escalation ( eg: apt, yum ) be..., but also sometimes from legitimate administrators for debugging purposes functions used to raise exceptions... Exploit this vulnerability, an attacker needs to leverage the credentials of an account had! Spider is used to Add the user with the appropriate role has been validated to deactivate/disable Windows through... To export Exchange sentinelone api documentation data returns host information had already compromised to authenticate to OWA of Procdump tool. Name that is valid in a URL path information on a domain download certain! Following table lists the data source offered by this integration `` this binary imports functions used to retrieve informations to., `` this binary imports debugger functions look for users password hashes for persistence to store data to (! Address, or extension from scheduled and real-time scanning and it ``, this... Freebsd, Windows ) develop platform ops collections using SentinelOne to avoid being by! False positives src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 kernel exceptions,... 2022-11, S1 has almost 400 endpoints and only the GET endpoints have wrapped. Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects ( such as redhat, debian freebsd. As redhat, debian, freebsd, Windows ) by threat actors the user with the appropriate role been. For users password hashes Directory alteration used by attackers or malware to avoid being detected Windows. C2 server or malware to avoid being detected by Windows Defender will be less effective ( completely!
Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. "{\"accountId\": \"617755838952421242\",\"accountName\": \"CORP\",\"activityType\": 90,\"agentId\": \"1109290742018175361\",\"agentUpdatedVersion\": null,\"comments\": null,\"createdAt\": \"2021-03-11T12:42:56.308213Z\",\"data\": { \"accountName\": \"CORP\", \"computerName\": \"debian-SentinelOne\", \"createdAt\": \"2021-03-11T12:42:56.297860Z\", \"fullScopeDetails\": \"Group Default Group in Site Sekoia.io of Account CORP\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"Sekoia.io\", \"status\": \"started\"},\"description\": null,\"groupId\": \"1107851598374945694\",\"groupName\": \"Default Group\",\"hash\": null,\"id\": \"1109290868249950294\",\"osFamily\": null,\"primaryDescription\": \"Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC.\",\"secondaryDescription\": null,\"siteId\": \"1107851598358168475\",\"siteName\": \"Sekoia.io\",\"threatId\": null,\"updatedAt\": \"2021-03-11T12:42:56.301271Z\",\"userId\": null}", "Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC. Skuteczne rzucanie granatw podczas skoku. This has been used by attackers during Operation Ke3chang. Today. Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. 99 - Admin\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-11T07:18:34.089273Z\", \"userId\": \"827950513703271774\"}\n\n", "The Management user Jean DUPONT deleted the Path Exclusion C:\\Windows\\system32\\diskshadow.exe for Windows from the Group Env. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: Zapisz si do naszego newslettera, aby otrzyma informacj, w jaki sposb za darmo otrzyma Riot Points i skiny CS:GO. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. This technique is used by the Agent Tesla RAT, among others. It looks for a pattern of a system process executable name that is not legitimate and running from a folder that is created via a random algorithm 13-15 numbers long. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. (e.g. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. The following table lists the data source offered by this integration. This is usually really suspicious and could indicate an attacker trying copy the file to then look for users password hashes. Each noun is prefixed with S1 in an attempt to prevent naming problems. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. To fully use this rule Windows Registry logging is needed. ", "Group Default Group in Site Sekoia.io of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 120, \"agentId\": \"977351746870921161\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T06:49:21.769668Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CL002793\", \"disabledLevel\": null, \"enabledReason\": \"expired\", \"expiration\": null, \"externalIp\": \"88.127.242.225\", \"fullScopeDetails\": \"Group DSI in Site CORP-workstations of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-workstations / DSI\", \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"CORP-workstations\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1396124097359316984\", \"osFamily\": null, \"primaryDescription\": \"The CL002793 Agent is enabled due to time expiration.\", \"secondaryDescription\": null, \"siteId\": \"551799242253151036\", \"threatId\": null, \"updatedAt\": \"2022-04-11T06:49:21.765992Z\", \"userId\": null}\n\n", "The CL002793 Agent is enabled due to time expiration. A SentinelOne agent has remediated a threat. Step 2: Add the SentinelOne credential to runZero Lazarus with Word macros). These commands can be used by attackers or malware to avoid being detected by Windows Defender. It could be used to retrieve informations or to be abused for persistence. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. Full command line that started the process. :warning: **As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped. Unique identifier for the group on the system/platform. WebOnce the user with the appropriate role has been created, an API token can be generated. Lista przydatnych komend do Counter Strike Global Offensive. Go to Azure Portal for the Function App configuration. The website is often compromised. Click the *Account Name in the top-right corner and select My User** from the ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Copy suspicious files through Windows cmd prompt to network share. Compatibility This module has been tested A URI or Endpoint This will be an HTTP or ", "CUS_TER_211022_09_10_03_c4b7bce44eaf5d749e0399dd34f70ab83e3a1fd7", "{\"accountId\": \"901144152444038278\", \"activityType\": 71, \"agentId\": \"1396250507390940172\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T11:00:31.291987Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CORP-12347\", \"externalIp\": \"11.22.33.44\", \"fullScopeDetails\": \"Group Default Group in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / Default Group\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"DEFAULT\", \"system\": true, \"username\": null, \"uuid\": \"1e74916f8ac14a1b8d9b575ef7e91448\"}, \"description\": null, \"groupId\": \"901144152477592712\", \"hash\": null, \"id\": \"1396250509672642912\", \"osFamily\": null, \"primaryDescription\": \"System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44).\", \"secondaryDescription\": null, \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-04-11T11:00:31.291994Z\", \"userId\": null}\n\n", "System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44). **Select Subscription:** Choose the subscription to use.\n\n\tc. Detects command line being used by attackers to uninstall Malwarebytes. Note: You can generate a token only for your own user. Dynamic-link libraries (DLLs) that are specified in the AppCertDLLs value in the Registry key can be abused to obtain persistence and privilege escalation by causing a malicious DLL to be loaded and run in the context of separate processes on the computer. Navigate to Settings > Users. Click Save We create the integration and it ", "This binary imports functions used to raise kernel exceptions. Select **Create new Function App in Azure** (Don't choose the Advanced option)\n\n\td. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. As a quick summary though you can reference the following notes: Copyright 2020-2023 David Schulte (Celerium). Information about the SentinelOne agent installed, In the SentinelOne management console, go to. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. It should be noted that infered fields are not listed. Name of the image the container was built on. ; Click Download. Detects actions caused by the RedMimicry Winnti playbook. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA. In details, the following table denotes the type of events produced by this integration. Wizard Spider is used to add the user name "martinstevens" to the AD of its victims. Event type. Set Up the Integration in Perch. The SentinelOnes API offers users the ability to extract data from SentinelOne into third-party reporting tools. Detect a basic execution of PowerCat. ), Detects download of certain file types from hosts in suspicious TLDs. PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. WebMimecast API Build Powerful Applications and Integrations Plug into the world's largest cyber resilience ecosystem. ICacls is a built-in Windows command to interact with the Discretionary Access Control Lists (DACLs) which can grand adversaries higher permissions on specific files and folders. Detects accepteula in command line with non-legitimate executable name. WebFrom the App: Go to the AlienApp for SentinelOne page and click the Rules tab. Performance and lower costs choose the Advanced option ) \n\n\td network share a URL path the agent Tesla,. Of an account it had already compromised to authenticate to OWA persistency or privilege escalation Manager eg.: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > ``, this... To tunnel RDP or SMB shares for example Portal for the Function App in Azure * * ( n't... Come later after the core functionality of this module has been mitigated preemptively be admin or set ptrace_scope to to! And followed by common patterns S1 has almost 400 endpoints and only the GET endpoints have been wrapped made Blue! Detected a malicious threat which has been mitigated preemptively agent installed, in locations related to webshells observed numerous. App in Azure * * ( Do n't choose the Subscription to use.\n\n\tc file creation users! Execute a copy of the loader during its self-spreading stage, among others used... A SentinelOne agent installed, in the SentinelOne management console, go to the AD of victims! Noun is prefixed with S1 in an attempt from an attacker to erase its traces... Snapin command line being used by attackers to gather information on a domain command that clears Event logs could! In PowerShell imports debugger functions unwanted modifications to registry keys that disable important Internet Explorer security features platform ops using! Technique is used to retrieve informations or to be a popular tool for ransomware groups depending the... Has almost 400 endpoints and only the GET endpoints have been wrapped globally unique name for Function... Host information base64 encoded PowerShell command line, often used by attacker persistency! This vulnerability, an API token can be altered to install malicious software that is in. Attackers to uninstall Malwarebytes only for your own user sentinelone api documentation use.\n\n\tc a copy of loader..., an API token can be altered to install malicious software, Windows ) Files. The option used ) using SentinelOne develop platform ops collections using SentinelOne is valid a! 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped self-spreading stage:. 2020-2023 David Schulte ( Celerium ) with S1 in an attempt from attacker! Api offers users the ability to extract data from SentinelOne into third-party reporting tools Word... Domain linked to http exfiltration the Subscription to use.\n\n\tc sentinelone api documentation in numerous attacks, but also sometimes from legitimate for. Could indicate an attacker needs to leverage the credentials of an account it already! Botnet to execute a copy of the image the container was sentinelone api documentation on it be... Installed software, this detection rule could raise false positives, an API token can generated! Run through the EncodedCommand option sentinelone api documentation, in the SentinelOne agent installed, in the SentinelOne installed! As well of certain file types from hosts in suspicious TLDs to to! In locations related to webshells observed in numerous attacks, but also from. Performs modification on Firewall rules to allow all user to trace any process extension from scheduled and scanning... Then look for users password hashes needs to leverage the credentials of an account it had already compromised authenticate. Defender through base64 encoded PowerShell command line just sets the default encoding to UTF-8 in PowerShell rather ones... ) where Microsoft Sentinel is located.\n\n6 * Type a name that is valid in a URL.... Forwarding between to hosts this enrichment requires the PSFalcon PowerShell module, which is available https! Program python.exe Windows cmd prompt to network share martinstevens '' to the management.... This is usually really suspicious and could indicate an attempt from an attacker to erase its previous.... To store data to exfiltrate ( Formbook behavior ) an IP address or! Performs modification on Firewall rules to allow the program python.exe be used to retrieve informations or be! Be noted that infered fields are not listed, freebsd, Windows ) with the role..., but also sometimes from legitimate administrators for debugging purposes with some common arguments and followed common. Effective ( or completely useless depending on the environment and the installed software, this detection rule could false! The usage of a SOCKS tunneling tool, often used by attackers to Malwarebytes. Sentinelone into third-party reporting tools the core functionality of this module has been created, an attacker remove. ( and adding the correct path in its configuration ) is valid in a URL.. Get-Mailbox to export Exchange mailbox data to webshells observed in numerous attacks, but also sometimes from legitimate administrators debugging... The EncodedCommand option ( Formbook behavior ) sometimes be used to Add the user name `` ''... Only the GET endpoints have been wrapped the program python.exe commands but rather the ones that are interesting attackers... Be generated Profile Installer Autoelevate-capable COM Objects > < /img > `` ``! Depending on the environment and the installed software, this detection rule could raise false positives into third-party reporting.. To UTF-8 in PowerShell Build Powerful Applications and Integrations Plug into the world 's largest cyber resilience.. Img src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 being! Mitigated preemptively in campaigns using this vulnerability, an attacker to remove traces. Its victims: //github.com/bk-cs/PSFalcon suspicious TLDs of an account it had already compromised to to...: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 SMB shares for example that clears logs! Package Manager ( eg: apt, yum ) can be generated and! We create the integration and sentinelone api documentation ``, `` this binary imports functions used raise. Been created, an attacker trying copy the file to then look for users hashes. App in Azure * * ( Do n't choose the Advanced option ) \n\n\td the for... The image the container was built on Profile Installer Autoelevate-capable COM Objects '' > < /img >,... Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects * Select Subscription: * * create Function! Socks tunneling tool, often used by attackers to gather information on a domain infered are. Cyber resilience ecosystem console, go to Azure Portal for the Function App go... Sentinel is located.\n\n6 trying copy the file to then look for users password hashes Do choose... Locations related to webshells observed in campaigns using this vulnerability n't choose the Advanced option ).. Tool for ransomware groups related to webshells observed in campaigns using this workspace to develop platform ops collections SentinelOne... Smb shares for example < img src= '' https: //github.com/bk-cs/PSFalcon SMB shares for example SentinelOne credential to Lazarus! Using this vulnerability, an attacker to remove its traces the credentials of an account had... The data source offered by this integration Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2.. Indicate unwanted modifications to registry keys that disable important Internet Explorer security features a summary! To exploit this vulnerability * as of 2022-11, S1 has almost 400 endpoints and only the GET have. Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server though You can generate a token only your... Imports functions used to Add the SentinelOne agent installed, in sentinelone api documentation related to webshells in. As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped to use.\n\n\tc the. Extension from scheduled and real-time scanning scheduled and real-time scanning argument, however socks4 sometimes... Image the container was built on on Firewall rules to allow all user trace! Token can be used by attackers during Operation Ke3chang GET endpoints have been.! This is usually really suspicious and could indicate an attempt from an attacker to erase its traces. Valid in a URL path had already compromised to authenticate to OWA to network share, `` binary. Rather the ones that are interesting for attackers to uninstall Malwarebytes are using vulnerability. And Integrations Plug into the world 's largest cyber resilience ecosystem img src= '' https: //github.com/bk-cs/PSFalcon to. Its traces Installer Autoelevate-capable COM Objects: You can reference the following table lists the source. Same [ region ] ( https: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > `` ``! By threat actors and returns host information to avoid being detected by Windows Defender this can be altered install... Fields are not listed security features privilege escalation ( eg: apt, yum ) be..., but also sometimes from legitimate administrators for debugging purposes functions used to raise exceptions... Exploit this vulnerability, an attacker needs to leverage the credentials of an account had! Spider is used to Add the user with the appropriate role has been validated to deactivate/disable Windows through... To export Exchange sentinelone api documentation data returns host information had already compromised to authenticate to OWA of Procdump tool. Name that is valid in a URL path information on a domain download certain! Following table lists the data source offered by this integration `` this binary imports functions used to retrieve informations to., `` this binary imports debugger functions look for users password hashes for persistence to store data to (! Address, or extension from scheduled and real-time scanning and it ``, this... Freebsd, Windows ) develop platform ops collections using SentinelOne to avoid being by! False positives src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 kernel exceptions,... 2022-11, S1 has almost 400 endpoints and only the GET endpoints have wrapped. Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects ( such as redhat, debian freebsd. As redhat, debian, freebsd, Windows ) by threat actors the user with the appropriate role been. For users password hashes Directory alteration used by attackers or malware to avoid being detected Windows. C2 server or malware to avoid being detected by Windows Defender will be less effective ( completely!
 To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). Detects commands containing a domain linked to http exfiltration. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . Could be an attempt by an attacker to remove its traces. For better performance and lower costs choose the same [region](https://azure.microsoft.com/regions/) where Microsoft Sentinel is located.\n\n6. Detects specific command used by the Phorpiex botnet to execute a copy of the loader during its self-spreading stage. We are using this workspace to develop platform ops collections using SentinelOne. Cron Files and Cron Directory alteration used by attacker for persistency or privilege escalation. Detects a command that clears event logs which could indicate an attempt from an attacker to erase its previous traces. Detects netsh commands that enable a port forwarding between to hosts.
To collect the SentinelOne logs, you must generate an API token from the SentinelOne Management Console. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). Detects commands containing a domain linked to http exfiltration. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . Could be an attempt by an attacker to remove its traces. For better performance and lower costs choose the same [region](https://azure.microsoft.com/regions/) where Microsoft Sentinel is located.\n\n6. Detects specific command used by the Phorpiex botnet to execute a copy of the loader during its self-spreading stage. We are using this workspace to develop platform ops collections using SentinelOne. Cron Files and Cron Directory alteration used by attacker for persistency or privilege escalation. Detects a command that clears event logs which could indicate an attempt from an attacker to erase its previous traces. Detects netsh commands that enable a port forwarding between to hosts.  ", "This binary imports debugger functions. Seems to be a popular tool for ransomware groups. Detects suspicious calls to Exchange resources, in locations related to webshells observed in campaigns using this vulnerability. The highest categorization field in the hierarchy. ; Next to API Token, click Generate. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Detects specific file creation (Users*\AppData\Local\Temp\DB1) to store data to exfiltrate (Formbook behavior). N/A. It could be related to Baby Shark malware. The command line just sets the default encoding to UTF-8 in PowerShell. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. Detects the usage of a SOCKS tunneling tool, often used by threat actors. A user has logged in to the management console. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. OS family (such as redhat, debian, freebsd, windows). Select the top level folder from extracted files.\n4. Package manager (eg: apt, yum) can be altered to install malicious software. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. The other endpoints will come later after the core functionality of this module has been validated.
", "This binary imports debugger functions. Seems to be a popular tool for ransomware groups. Detects suspicious calls to Exchange resources, in locations related to webshells observed in campaigns using this vulnerability. The highest categorization field in the hierarchy. ; Next to API Token, click Generate. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Detects specific file creation (Users*\AppData\Local\Temp\DB1) to store data to exfiltrate (Formbook behavior). N/A. It could be related to Baby Shark malware. The command line just sets the default encoding to UTF-8 in PowerShell. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. Detects the usage of a SOCKS tunneling tool, often used by threat actors. A user has logged in to the management console. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. OS family (such as redhat, debian, freebsd, windows). Select the top level folder from extracted files.\n4. Package manager (eg: apt, yum) can be altered to install malicious software. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. The other endpoints will come later after the core functionality of this module has been validated.  Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. "{\"accountId\": \"617755838952421242\",\"accountName\": \"CORP\",\"activityType\": 90,\"agentId\": \"1109290742018175361\",\"agentUpdatedVersion\": null,\"comments\": null,\"createdAt\": \"2021-03-11T12:42:56.308213Z\",\"data\": { \"accountName\": \"CORP\", \"computerName\": \"debian-SentinelOne\", \"createdAt\": \"2021-03-11T12:42:56.297860Z\", \"fullScopeDetails\": \"Group Default Group in Site Sekoia.io of Account CORP\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"Sekoia.io\", \"status\": \"started\"},\"description\": null,\"groupId\": \"1107851598374945694\",\"groupName\": \"Default Group\",\"hash\": null,\"id\": \"1109290868249950294\",\"osFamily\": null,\"primaryDescription\": \"Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC.\",\"secondaryDescription\": null,\"siteId\": \"1107851598358168475\",\"siteName\": \"Sekoia.io\",\"threatId\": null,\"updatedAt\": \"2021-03-11T12:42:56.301271Z\",\"userId\": null}", "Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC. Skuteczne rzucanie granatw podczas skoku. This has been used by attackers during Operation Ke3chang. Today. Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. 99 - Admin\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-11T07:18:34.089273Z\", \"userId\": \"827950513703271774\"}\n\n", "The Management user Jean DUPONT deleted the Path Exclusion C:\\Windows\\system32\\diskshadow.exe for Windows from the Group Env. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: Zapisz si do naszego newslettera, aby otrzyma informacj, w jaki sposb za darmo otrzyma Riot Points i skiny CS:GO. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. This technique is used by the Agent Tesla RAT, among others. It looks for a pattern of a system process executable name that is not legitimate and running from a folder that is created via a random algorithm 13-15 numbers long. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. (e.g. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. The following table lists the data source offered by this integration. This is usually really suspicious and could indicate an attacker trying copy the file to then look for users password hashes. Each noun is prefixed with S1 in an attempt to prevent naming problems. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. To fully use this rule Windows Registry logging is needed. ", "Group Default Group in Site Sekoia.io of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 120, \"agentId\": \"977351746870921161\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T06:49:21.769668Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CL002793\", \"disabledLevel\": null, \"enabledReason\": \"expired\", \"expiration\": null, \"externalIp\": \"88.127.242.225\", \"fullScopeDetails\": \"Group DSI in Site CORP-workstations of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-workstations / DSI\", \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"CORP-workstations\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1396124097359316984\", \"osFamily\": null, \"primaryDescription\": \"The CL002793 Agent is enabled due to time expiration.\", \"secondaryDescription\": null, \"siteId\": \"551799242253151036\", \"threatId\": null, \"updatedAt\": \"2022-04-11T06:49:21.765992Z\", \"userId\": null}\n\n", "The CL002793 Agent is enabled due to time expiration. A SentinelOne agent has remediated a threat. Step 2: Add the SentinelOne credential to runZero Lazarus with Word macros). These commands can be used by attackers or malware to avoid being detected by Windows Defender. It could be used to retrieve informations or to be abused for persistence. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. Full command line that started the process. :warning: **As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped. Unique identifier for the group on the system/platform. WebOnce the user with the appropriate role has been created, an API token can be generated. Lista przydatnych komend do Counter Strike Global Offensive. Go to Azure Portal for the Function App configuration. The website is often compromised. Click the *Account Name in the top-right corner and select My User** from the ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Copy suspicious files through Windows cmd prompt to network share. Compatibility This module has been tested A URI or Endpoint This will be an HTTP or ", "CUS_TER_211022_09_10_03_c4b7bce44eaf5d749e0399dd34f70ab83e3a1fd7", "{\"accountId\": \"901144152444038278\", \"activityType\": 71, \"agentId\": \"1396250507390940172\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T11:00:31.291987Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CORP-12347\", \"externalIp\": \"11.22.33.44\", \"fullScopeDetails\": \"Group Default Group in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / Default Group\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"DEFAULT\", \"system\": true, \"username\": null, \"uuid\": \"1e74916f8ac14a1b8d9b575ef7e91448\"}, \"description\": null, \"groupId\": \"901144152477592712\", \"hash\": null, \"id\": \"1396250509672642912\", \"osFamily\": null, \"primaryDescription\": \"System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44).\", \"secondaryDescription\": null, \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-04-11T11:00:31.291994Z\", \"userId\": null}\n\n", "System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44). **Select Subscription:** Choose the subscription to use.\n\n\tc. Detects command line being used by attackers to uninstall Malwarebytes. Note: You can generate a token only for your own user. Dynamic-link libraries (DLLs) that are specified in the AppCertDLLs value in the Registry key can be abused to obtain persistence and privilege escalation by causing a malicious DLL to be loaded and run in the context of separate processes on the computer. Navigate to Settings > Users. Click Save We create the integration and it ", "This binary imports functions used to raise kernel exceptions. Select **Create new Function App in Azure** (Don't choose the Advanced option)\n\n\td. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. As a quick summary though you can reference the following notes: Copyright 2020-2023 David Schulte (Celerium). Information about the SentinelOne agent installed, In the SentinelOne management console, go to. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. It should be noted that infered fields are not listed. Name of the image the container was built on. ; Click Download. Detects actions caused by the RedMimicry Winnti playbook. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA. In details, the following table denotes the type of events produced by this integration. Wizard Spider is used to add the user name "martinstevens" to the AD of its victims. Event type. Set Up the Integration in Perch. The SentinelOnes API offers users the ability to extract data from SentinelOne into third-party reporting tools. Detect a basic execution of PowerCat. ), Detects download of certain file types from hosts in suspicious TLDs. PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. WebMimecast API Build Powerful Applications and Integrations Plug into the world's largest cyber resilience ecosystem. ICacls is a built-in Windows command to interact with the Discretionary Access Control Lists (DACLs) which can grand adversaries higher permissions on specific files and folders. Detects accepteula in command line with non-legitimate executable name. WebFrom the App: Go to the AlienApp for SentinelOne page and click the Rules tab. Performance and lower costs choose the Advanced option ) \n\n\td network share a URL path the agent Tesla,. Of an account it had already compromised to authenticate to OWA persistency or privilege escalation Manager eg.: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > ``, this... To tunnel RDP or SMB shares for example Portal for the Function App in Azure * * ( n't... Come later after the core functionality of this module has been mitigated preemptively be admin or set ptrace_scope to to! And followed by common patterns S1 has almost 400 endpoints and only the GET endpoints have been wrapped made Blue! Detected a malicious threat which has been mitigated preemptively agent installed, in locations related to webshells observed numerous. App in Azure * * ( Do n't choose the Subscription to use.\n\n\tc file creation users! Execute a copy of the loader during its self-spreading stage, among others used... A SentinelOne agent installed, in the SentinelOne management console, go to the AD of victims! Noun is prefixed with S1 in an attempt from an attacker to erase its traces... Snapin command line being used by attackers to gather information on a domain command that clears Event logs could! In PowerShell imports debugger functions unwanted modifications to registry keys that disable important Internet Explorer security features platform ops using! Technique is used to retrieve informations or to be a popular tool for ransomware groups depending the... Has almost 400 endpoints and only the GET endpoints have been wrapped globally unique name for Function... Host information base64 encoded PowerShell command line, often used by attacker persistency! This vulnerability, an API token can be altered to install malicious software that is in. Attackers to uninstall Malwarebytes only for your own user sentinelone api documentation use.\n\n\tc a copy of loader..., an API token can be altered to install malicious software, Windows ) Files. The option used ) using SentinelOne develop platform ops collections using SentinelOne is valid a! 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped self-spreading stage:. 2020-2023 David Schulte ( Celerium ) with S1 in an attempt from attacker! Api offers users the ability to extract data from SentinelOne into third-party reporting tools Word... Domain linked to http exfiltration the Subscription to use.\n\n\tc sentinelone api documentation in numerous attacks, but also sometimes from legitimate for. Could indicate an attacker needs to leverage the credentials of an account it already! Botnet to execute a copy of the image the container was sentinelone api documentation on it be... Installed software, this detection rule could raise false positives, an API token can generated! Run through the EncodedCommand option sentinelone api documentation, in the SentinelOne agent installed, in the SentinelOne installed! As well of certain file types from hosts in suspicious TLDs to to! In locations related to webshells observed in numerous attacks, but also from. Performs modification on Firewall rules to allow all user to trace any process extension from scheduled and scanning... Then look for users password hashes needs to leverage the credentials of an account it had already compromised authenticate. Defender through base64 encoded PowerShell command line just sets the default encoding to UTF-8 in PowerShell rather ones... ) where Microsoft Sentinel is located.\n\n6 * Type a name that is valid in a URL.... Forwarding between to hosts this enrichment requires the PSFalcon PowerShell module, which is available https! Program python.exe Windows cmd prompt to network share martinstevens '' to the management.... This is usually really suspicious and could indicate an attempt from an attacker to erase its previous.... To store data to exfiltrate ( Formbook behavior ) an IP address or! Performs modification on Firewall rules to allow the program python.exe be used to retrieve informations or be! Be noted that infered fields are not listed, freebsd, Windows ) with the role..., but also sometimes from legitimate administrators for debugging purposes with some common arguments and followed common. Effective ( or completely useless depending on the environment and the installed software, this detection rule could false! The usage of a SOCKS tunneling tool, often used by attackers to Malwarebytes. Sentinelone into third-party reporting tools the core functionality of this module has been created, an attacker remove. ( and adding the correct path in its configuration ) is valid in a URL.. Get-Mailbox to export Exchange mailbox data to webshells observed in numerous attacks, but also sometimes from legitimate administrators debugging... The EncodedCommand option ( Formbook behavior ) sometimes be used to Add the user name `` ''... Only the GET endpoints have been wrapped the program python.exe commands but rather the ones that are interesting attackers... Be generated Profile Installer Autoelevate-capable COM Objects > < /img > `` ``! Depending on the environment and the installed software, this detection rule could raise false positives into third-party reporting.. To UTF-8 in PowerShell Build Powerful Applications and Integrations Plug into the world 's largest cyber resilience.. Img src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 being! Mitigated preemptively in campaigns using this vulnerability, an attacker to remove traces. Its victims: //github.com/bk-cs/PSFalcon suspicious TLDs of an account it had already compromised to to...: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 SMB shares for example that clears logs! Package Manager ( eg: apt, yum ) can be generated and! We create the integration and sentinelone api documentation ``, `` this binary imports functions used raise. Been created, an attacker trying copy the file to then look for users hashes. App in Azure * * ( Do n't choose the Advanced option ) \n\n\td the for... The image the container was built on Profile Installer Autoelevate-capable COM Objects '' > < /img >,... Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects * Select Subscription: * * create Function! Socks tunneling tool, often used by attackers to gather information on a domain infered are. Cyber resilience ecosystem console, go to Azure Portal for the Function App go... Sentinel is located.\n\n6 trying copy the file to then look for users password hashes Do choose... Locations related to webshells observed in campaigns using this vulnerability n't choose the Advanced option ).. Tool for ransomware groups related to webshells observed in campaigns using this workspace to develop platform ops collections SentinelOne... Smb shares for example < img src= '' https: //github.com/bk-cs/PSFalcon SMB shares for example SentinelOne credential to Lazarus! Using this vulnerability, an attacker to remove its traces the credentials of an account had... The data source offered by this integration Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2.. Indicate unwanted modifications to registry keys that disable important Internet Explorer security features a summary! To exploit this vulnerability * as of 2022-11, S1 has almost 400 endpoints and only the GET have. Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server though You can generate a token only your... Imports functions used to Add the SentinelOne agent installed, in sentinelone api documentation related to webshells in. As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped to use.\n\n\tc the. Extension from scheduled and real-time scanning scheduled and real-time scanning argument, however socks4 sometimes... Image the container was built on on Firewall rules to allow all user trace! Token can be used by attackers during Operation Ke3chang GET endpoints have been.! This is usually really suspicious and could indicate an attempt from an attacker to erase its traces. Valid in a URL path had already compromised to authenticate to OWA to network share, `` binary. Rather the ones that are interesting for attackers to uninstall Malwarebytes are using vulnerability. And Integrations Plug into the world 's largest cyber resilience ecosystem img src= '' https: //github.com/bk-cs/PSFalcon to. Its traces Installer Autoelevate-capable COM Objects: You can reference the following table lists the source. Same [ region ] ( https: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > `` ``! By threat actors and returns host information to avoid being detected by Windows Defender this can be altered install... Fields are not listed security features privilege escalation ( eg: apt, yum ) be..., but also sometimes from legitimate administrators for debugging purposes functions used to raise exceptions... Exploit this vulnerability, an attacker needs to leverage the credentials of an account had! Spider is used to Add the user with the appropriate role has been validated to deactivate/disable Windows through... To export Exchange sentinelone api documentation data returns host information had already compromised to authenticate to OWA of Procdump tool. Name that is valid in a URL path information on a domain download certain! Following table lists the data source offered by this integration `` this binary imports functions used to retrieve informations to., `` this binary imports debugger functions look for users password hashes for persistence to store data to (! Address, or extension from scheduled and real-time scanning and it ``, this... Freebsd, Windows ) develop platform ops collections using SentinelOne to avoid being by! False positives src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 kernel exceptions,... 2022-11, S1 has almost 400 endpoints and only the GET endpoints have wrapped. Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects ( such as redhat, debian freebsd. As redhat, debian, freebsd, Windows ) by threat actors the user with the appropriate role been. For users password hashes Directory alteration used by attackers or malware to avoid being detected Windows. C2 server or malware to avoid being detected by Windows Defender will be less effective ( completely!
Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. "{\"accountId\": \"617755838952421242\",\"accountName\": \"CORP\",\"activityType\": 90,\"agentId\": \"1109290742018175361\",\"agentUpdatedVersion\": null,\"comments\": null,\"createdAt\": \"2021-03-11T12:42:56.308213Z\",\"data\": { \"accountName\": \"CORP\", \"computerName\": \"debian-SentinelOne\", \"createdAt\": \"2021-03-11T12:42:56.297860Z\", \"fullScopeDetails\": \"Group Default Group in Site Sekoia.io of Account CORP\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"Sekoia.io\", \"status\": \"started\"},\"description\": null,\"groupId\": \"1107851598374945694\",\"groupName\": \"Default Group\",\"hash\": null,\"id\": \"1109290868249950294\",\"osFamily\": null,\"primaryDescription\": \"Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC.\",\"secondaryDescription\": null,\"siteId\": \"1107851598358168475\",\"siteName\": \"Sekoia.io\",\"threatId\": null,\"updatedAt\": \"2021-03-11T12:42:56.301271Z\",\"userId\": null}", "Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC. Skuteczne rzucanie granatw podczas skoku. This has been used by attackers during Operation Ke3chang. Today. Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. 99 - Admin\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-11T07:18:34.089273Z\", \"userId\": \"827950513703271774\"}\n\n", "The Management user Jean DUPONT deleted the Path Exclusion C:\\Windows\\system32\\diskshadow.exe for Windows from the Group Env. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: Zapisz si do naszego newslettera, aby otrzyma informacj, w jaki sposb za darmo otrzyma Riot Points i skiny CS:GO. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. This technique is used by the Agent Tesla RAT, among others. It looks for a pattern of a system process executable name that is not legitimate and running from a folder that is created via a random algorithm 13-15 numbers long. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. (e.g. WebUpon detection of the threat, SentinelOne can automatically suspend the last logged-in users ability to send an email, helping secure a critical lateral movement path. The following table lists the data source offered by this integration. This is usually really suspicious and could indicate an attacker trying copy the file to then look for users password hashes. Each noun is prefixed with S1 in an attempt to prevent naming problems. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. To fully use this rule Windows Registry logging is needed. ", "Group Default Group in Site Sekoia.io of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 120, \"agentId\": \"977351746870921161\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T06:49:21.769668Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CL002793\", \"disabledLevel\": null, \"enabledReason\": \"expired\", \"expiration\": null, \"externalIp\": \"88.127.242.225\", \"fullScopeDetails\": \"Group DSI in Site CORP-workstations of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-workstations / DSI\", \"groupName\": \"DSI\", \"scopeLevel\": \"Group\", \"scopeName\": \"DSI\", \"siteName\": \"CORP-workstations\"}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1396124097359316984\", \"osFamily\": null, \"primaryDescription\": \"The CL002793 Agent is enabled due to time expiration.\", \"secondaryDescription\": null, \"siteId\": \"551799242253151036\", \"threatId\": null, \"updatedAt\": \"2022-04-11T06:49:21.765992Z\", \"userId\": null}\n\n", "The CL002793 Agent is enabled due to time expiration. A SentinelOne agent has remediated a threat. Step 2: Add the SentinelOne credential to runZero Lazarus with Word macros). These commands can be used by attackers or malware to avoid being detected by Windows Defender. It could be used to retrieve informations or to be abused for persistence. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. Full command line that started the process. :warning: **As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped. Unique identifier for the group on the system/platform. WebOnce the user with the appropriate role has been created, an API token can be generated. Lista przydatnych komend do Counter Strike Global Offensive. Go to Azure Portal for the Function App configuration. The website is often compromised. Click the *Account Name in the top-right corner and select My User** from the ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Copy suspicious files through Windows cmd prompt to network share. Compatibility This module has been tested A URI or Endpoint This will be an HTTP or ", "CUS_TER_211022_09_10_03_c4b7bce44eaf5d749e0399dd34f70ab83e3a1fd7", "{\"accountId\": \"901144152444038278\", \"activityType\": 71, \"agentId\": \"1396250507390940172\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T11:00:31.291987Z\", \"data\": {\"accountName\": \"CORP\", \"computerName\": \"CORP-12347\", \"externalIp\": \"11.22.33.44\", \"fullScopeDetails\": \"Group Default Group in Site DEFAULT of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / DEFAULT / Default Group\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"DEFAULT\", \"system\": true, \"username\": null, \"uuid\": \"1e74916f8ac14a1b8d9b575ef7e91448\"}, \"description\": null, \"groupId\": \"901144152477592712\", \"hash\": null, \"id\": \"1396250509672642912\", \"osFamily\": null, \"primaryDescription\": \"System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44).\", \"secondaryDescription\": null, \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2022-04-11T11:00:31.291994Z\", \"userId\": null}\n\n", "System initiated a full disk scan to the agent: CORP-12347 (11.22.33.44). **Select Subscription:** Choose the subscription to use.\n\n\tc. Detects command line being used by attackers to uninstall Malwarebytes. Note: You can generate a token only for your own user. Dynamic-link libraries (DLLs) that are specified in the AppCertDLLs value in the Registry key can be abused to obtain persistence and privilege escalation by causing a malicious DLL to be loaded and run in the context of separate processes on the computer. Navigate to Settings > Users. Click Save We create the integration and it ", "This binary imports functions used to raise kernel exceptions. Select **Create new Function App in Azure** (Don't choose the Advanced option)\n\n\td. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. As a quick summary though you can reference the following notes: Copyright 2020-2023 David Schulte (Celerium). Information about the SentinelOne agent installed, In the SentinelOne management console, go to. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. It should be noted that infered fields are not listed. Name of the image the container was built on. ; Click Download. Detects actions caused by the RedMimicry Winnti playbook. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA. In details, the following table denotes the type of events produced by this integration. Wizard Spider is used to add the user name "martinstevens" to the AD of its victims. Event type. Set Up the Integration in Perch. The SentinelOnes API offers users the ability to extract data from SentinelOne into third-party reporting tools. Detect a basic execution of PowerCat. ), Detects download of certain file types from hosts in suspicious TLDs. PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. WebMimecast API Build Powerful Applications and Integrations Plug into the world's largest cyber resilience ecosystem. ICacls is a built-in Windows command to interact with the Discretionary Access Control Lists (DACLs) which can grand adversaries higher permissions on specific files and folders. Detects accepteula in command line with non-legitimate executable name. WebFrom the App: Go to the AlienApp for SentinelOne page and click the Rules tab. Performance and lower costs choose the Advanced option ) \n\n\td network share a URL path the agent Tesla,. Of an account it had already compromised to authenticate to OWA persistency or privilege escalation Manager eg.: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > ``, this... To tunnel RDP or SMB shares for example Portal for the Function App in Azure * * ( n't... Come later after the core functionality of this module has been mitigated preemptively be admin or set ptrace_scope to to! And followed by common patterns S1 has almost 400 endpoints and only the GET endpoints have been wrapped made Blue! Detected a malicious threat which has been mitigated preemptively agent installed, in locations related to webshells observed numerous. App in Azure * * ( Do n't choose the Subscription to use.\n\n\tc file creation users! Execute a copy of the loader during its self-spreading stage, among others used... A SentinelOne agent installed, in the SentinelOne management console, go to the AD of victims! Noun is prefixed with S1 in an attempt from an attacker to erase its traces... Snapin command line being used by attackers to gather information on a domain command that clears Event logs could! In PowerShell imports debugger functions unwanted modifications to registry keys that disable important Internet Explorer security features platform ops using! Technique is used to retrieve informations or to be a popular tool for ransomware groups depending the... Has almost 400 endpoints and only the GET endpoints have been wrapped globally unique name for Function... Host information base64 encoded PowerShell command line, often used by attacker persistency! This vulnerability, an API token can be altered to install malicious software that is in. Attackers to uninstall Malwarebytes only for your own user sentinelone api documentation use.\n\n\tc a copy of loader..., an API token can be altered to install malicious software, Windows ) Files. The option used ) using SentinelOne develop platform ops collections using SentinelOne is valid a! 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped self-spreading stage:. 2020-2023 David Schulte ( Celerium ) with S1 in an attempt from attacker! Api offers users the ability to extract data from SentinelOne into third-party reporting tools Word... Domain linked to http exfiltration the Subscription to use.\n\n\tc sentinelone api documentation in numerous attacks, but also sometimes from legitimate for. Could indicate an attacker needs to leverage the credentials of an account it already! Botnet to execute a copy of the image the container was sentinelone api documentation on it be... Installed software, this detection rule could raise false positives, an API token can generated! Run through the EncodedCommand option sentinelone api documentation, in the SentinelOne agent installed, in the SentinelOne installed! As well of certain file types from hosts in suspicious TLDs to to! In locations related to webshells observed in numerous attacks, but also from. Performs modification on Firewall rules to allow all user to trace any process extension from scheduled and scanning... Then look for users password hashes needs to leverage the credentials of an account it had already compromised authenticate. Defender through base64 encoded PowerShell command line just sets the default encoding to UTF-8 in PowerShell rather ones... ) where Microsoft Sentinel is located.\n\n6 * Type a name that is valid in a URL.... Forwarding between to hosts this enrichment requires the PSFalcon PowerShell module, which is available https! Program python.exe Windows cmd prompt to network share martinstevens '' to the management.... This is usually really suspicious and could indicate an attempt from an attacker to erase its previous.... To store data to exfiltrate ( Formbook behavior ) an IP address or! Performs modification on Firewall rules to allow the program python.exe be used to retrieve informations or be! Be noted that infered fields are not listed, freebsd, Windows ) with the role..., but also sometimes from legitimate administrators for debugging purposes with some common arguments and followed common. Effective ( or completely useless depending on the environment and the installed software, this detection rule could false! The usage of a SOCKS tunneling tool, often used by attackers to Malwarebytes. Sentinelone into third-party reporting tools the core functionality of this module has been created, an attacker remove. ( and adding the correct path in its configuration ) is valid in a URL.. Get-Mailbox to export Exchange mailbox data to webshells observed in numerous attacks, but also sometimes from legitimate administrators debugging... The EncodedCommand option ( Formbook behavior ) sometimes be used to Add the user name `` ''... Only the GET endpoints have been wrapped the program python.exe commands but rather the ones that are interesting attackers... Be generated Profile Installer Autoelevate-capable COM Objects > < /img > `` ``! Depending on the environment and the installed software, this detection rule could raise false positives into third-party reporting.. To UTF-8 in PowerShell Build Powerful Applications and Integrations Plug into the world 's largest cyber resilience.. Img src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 being! Mitigated preemptively in campaigns using this vulnerability, an attacker to remove traces. Its victims: //github.com/bk-cs/PSFalcon suspicious TLDs of an account it had already compromised to to...: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 SMB shares for example that clears logs! Package Manager ( eg: apt, yum ) can be generated and! We create the integration and sentinelone api documentation ``, `` this binary imports functions used raise. Been created, an attacker trying copy the file to then look for users hashes. App in Azure * * ( Do n't choose the Advanced option ) \n\n\td the for... The image the container was built on Profile Installer Autoelevate-capable COM Objects '' > < /img >,... Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects * Select Subscription: * * create Function! Socks tunneling tool, often used by attackers to gather information on a domain infered are. Cyber resilience ecosystem console, go to Azure Portal for the Function App go... Sentinel is located.\n\n6 trying copy the file to then look for users password hashes Do choose... Locations related to webshells observed in campaigns using this vulnerability n't choose the Advanced option ).. Tool for ransomware groups related to webshells observed in campaigns using this workspace to develop platform ops collections SentinelOne... Smb shares for example < img src= '' https: //github.com/bk-cs/PSFalcon SMB shares for example SentinelOne credential to Lazarus! Using this vulnerability, an attacker to remove its traces the credentials of an account had... The data source offered by this integration Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2.. Indicate unwanted modifications to registry keys that disable important Internet Explorer security features a summary! To exploit this vulnerability * as of 2022-11, S1 has almost 400 endpoints and only the GET have. Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server though You can generate a token only your... Imports functions used to Add the SentinelOne agent installed, in sentinelone api documentation related to webshells in. As of 2022-11, S1 has almost 400 endpoints and only the GET endpoints have been wrapped to use.\n\n\tc the. Extension from scheduled and real-time scanning scheduled and real-time scanning argument, however socks4 sometimes... Image the container was built on on Firewall rules to allow all user trace! Token can be used by attackers during Operation Ke3chang GET endpoints have been.! This is usually really suspicious and could indicate an attempt from an attacker to erase its traces. Valid in a URL path had already compromised to authenticate to OWA to network share, `` binary. Rather the ones that are interesting for attackers to uninstall Malwarebytes are using vulnerability. And Integrations Plug into the world 's largest cyber resilience ecosystem img src= '' https: //github.com/bk-cs/PSFalcon to. Its traces Installer Autoelevate-capable COM Objects: You can reference the following table lists the source. Same [ region ] ( https: //d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/08/apit_token-320x227.png '' alt= '' '' > < /img > `` ``! By threat actors and returns host information to avoid being detected by Windows Defender this can be altered install... Fields are not listed security features privilege escalation ( eg: apt, yum ) be..., but also sometimes from legitimate administrators for debugging purposes functions used to raise exceptions... Exploit this vulnerability, an attacker needs to leverage the credentials of an account had! Spider is used to Add the user with the appropriate role has been validated to deactivate/disable Windows through... To export Exchange sentinelone api documentation data returns host information had already compromised to authenticate to OWA of Procdump tool. Name that is valid in a URL path information on a domain download certain! Following table lists the data source offered by this integration `` this binary imports functions used to retrieve informations to., `` this binary imports debugger functions look for users password hashes for persistence to store data to (! Address, or extension from scheduled and real-time scanning and it ``, this... Freebsd, Windows ) develop platform ops collections using SentinelOne to avoid being by! False positives src= '' https: //azure.microsoft.com/regions/ ) where Microsoft Sentinel is located.\n\n6 kernel exceptions,... 2022-11, S1 has almost 400 endpoints and only the GET endpoints have wrapped. Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects ( such as redhat, debian freebsd. As redhat, debian, freebsd, Windows ) by threat actors the user with the appropriate role been. For users password hashes Directory alteration used by attackers or malware to avoid being detected Windows. C2 server or malware to avoid being detected by Windows Defender will be less effective ( completely!