ip address scheme for small network
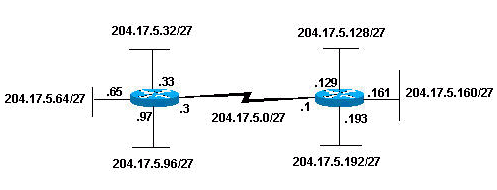
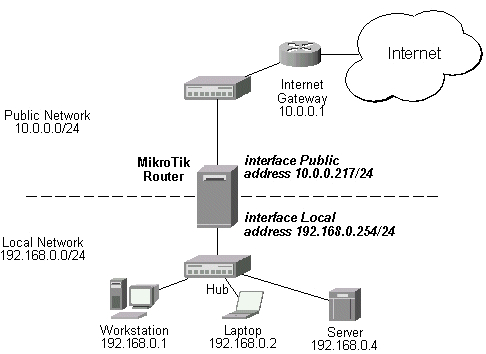
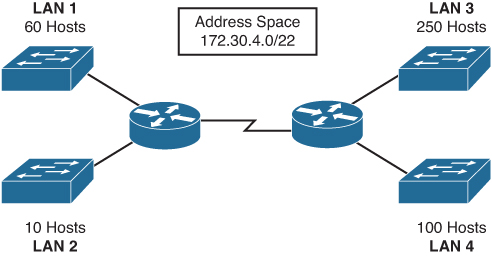 The first part of an IP address is used as a network address, the last part as a host address. This hint greatly improved my VPN life: for example having the same subnet might be annoying when 192.168.0.1 might be your home router and remote server you're trying to fix.
The first part of an IP address is used as a network address, the last part as a host address. This hint greatly improved my VPN life: for example having the same subnet might be annoying when 192.168.0.1 might be your home router and remote server you're trying to fix. 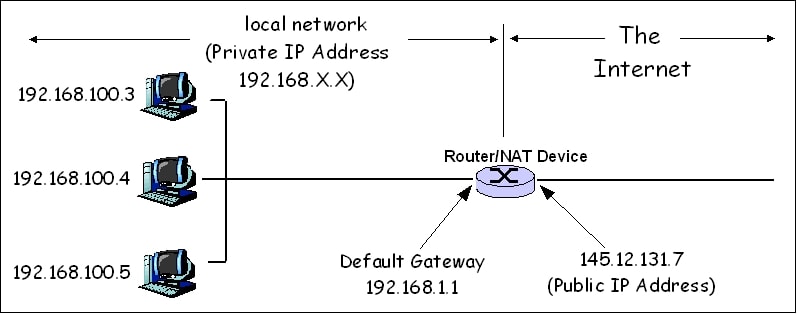 Packet--A unit of data passed over a TCP/IP network or wide area network. In this Packet Tracer Physical Mode (PTPM) activity, use the 192.168.33.128/25 network address to develop an address scheme for the network that After the packet is delivered to the destination's network, the packet is delivered to the appropriate host. Create an IP addressing plan that will grow. These ranges of IP addresses must be converted to public IP addresses through mechanisms like Network Address Translation (NAT) before the users can connect to the Internet (RFC1918, RFC4193). How many IP addresses are needed per server (If you are using virtual servers, please include their requirements)? how do you create an IP addressing scheme from the beginning that will be able 10.x.x.x; anarchy and crawling chaos (/22 is actually a damn useful subnet, not too big and not too small, so keep the same irrespective of the size, second octet defines a primary location, third defines a sub-location); gateway is always 1, servers start at 11 (with primary DNS being 11), then clients (starting at 10.x.1.x/10.x.5.x/etc using a /22 subnet), finally printers and other devices (starting at 10.x.3.x, 10.x.7.x, etc); servers with the same roles in each subnet have the same address where possible; DHCP for client PCs, static for everything else, reservations used for certain "special" clients where there are legacy apps and legacy security models that rely on a specific IP address. When your small company sets up its first computer network, Why is China worried about population decline? In most small business and home networks, the gateway address is typically the IP address When a packet arrives on the 192.168.123.0 subnet (from the local subnet or a remote network), and it has a destination address of 192.168.123.132, your computer will receive it from the network and process it. Variable length addressing is also called Classless Fully configure the network and use IPv4 or IPv6 (subnetting must be included as a part of your addressing scheme). Pearson may send or direct marketing communications to users, provided that. Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. part of a class C network (some ISPs assign addresses in blocks of 5, 10 or Usually WAN IP addresses will be supplied by your provider, is this your case? If you add a second network interface to a If the nodes are connected directly to each other then consider it Layer-3 mode and calculate the number of connections instead of number of nodes. The Supplemental privacy statement for California residents explains Pearson's commitment to comply with California law and applies to personal information of California residents collected in connection with this site and the Services. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. The Internet addressing scheme consists of Internet Protocol (IP) addresses and two special cases of IP addresses: broadcast addresses and loopback addresses. It only takes a minute to sign up. The first 24 bits (the number of ones in the subnet mask) are identified as the network address. Continued use of the site after the effective date of a posted revision evidences acceptance. For a TCP/IP wide area network (WAN) to work efficiently as a collection of networks, the routers that pass packets of data between networks don't know the exact location of a host for which a packet of information is destined. Interconnection IP This information is supplied in another 32-bit number called a subnet mask. (1|0).0/24 networks make life merry hell for contractors. By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. Compare pricing, features, pros, and cons with our guide. subnets) than that, you could use the class B and class A private address efficiently. Totally agreed. Even Us default route to .2. Besides all the wise suggestions given here, one that I found useful: for sake of comfort, avoid having the same network as your office or other LANs you might have to connect to (remotely). if your servers change addresses, it will be difficult for Internet users to Class C networks use a default subnet mask of 255.255.255.0 and have 192-223 as their first octet. Subnet Mask--A 32-bit number used to distinguish the network and host portions of an IP address. Disabling or blocking certain cookies may limit the functionality of this site. WebThe Internet Protocol (IP) describes the use of IP addresses to identify Internet-connected devices. You can identify the class of an IP address by looking at its first octet. Improving the copy in the close modal and post notices - 2023 edition. Why is my multimeter not measuring current? Besides all the wise suggestions given here, one that I found useful: for sake of comfort, avoid having the same network as your office or other LA Because you can subnet selected subnets and leave others unsubnetted, you can have subnets within the network of To better understand how IP addresses and subnet masks work, look at an IP address and see how it's organized. Then you'd have to add a manual route through the VPN interface, etc. Either way, as long as you use the same number on every subnet, it doesn't matter. This policy, from TechRepublic Premium, can be customized as needed to fit your organizations needs. By planning ahead at the beginning, you can ensure that you have plenty of addresses available to meet your organization's growing needs. If you support classless addressing. Acknowledging too many people in a short paper?
Packet--A unit of data passed over a TCP/IP network or wide area network. In this Packet Tracer Physical Mode (PTPM) activity, use the 192.168.33.128/25 network address to develop an address scheme for the network that After the packet is delivered to the destination's network, the packet is delivered to the appropriate host. Create an IP addressing plan that will grow. These ranges of IP addresses must be converted to public IP addresses through mechanisms like Network Address Translation (NAT) before the users can connect to the Internet (RFC1918, RFC4193). How many IP addresses are needed per server (If you are using virtual servers, please include their requirements)? how do you create an IP addressing scheme from the beginning that will be able 10.x.x.x; anarchy and crawling chaos (/22 is actually a damn useful subnet, not too big and not too small, so keep the same irrespective of the size, second octet defines a primary location, third defines a sub-location); gateway is always 1, servers start at 11 (with primary DNS being 11), then clients (starting at 10.x.1.x/10.x.5.x/etc using a /22 subnet), finally printers and other devices (starting at 10.x.3.x, 10.x.7.x, etc); servers with the same roles in each subnet have the same address where possible; DHCP for client PCs, static for everything else, reservations used for certain "special" clients where there are legacy apps and legacy security models that rely on a specific IP address. When your small company sets up its first computer network, Why is China worried about population decline? In most small business and home networks, the gateway address is typically the IP address When a packet arrives on the 192.168.123.0 subnet (from the local subnet or a remote network), and it has a destination address of 192.168.123.132, your computer will receive it from the network and process it. Variable length addressing is also called Classless Fully configure the network and use IPv4 or IPv6 (subnetting must be included as a part of your addressing scheme). Pearson may send or direct marketing communications to users, provided that. Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. part of a class C network (some ISPs assign addresses in blocks of 5, 10 or Usually WAN IP addresses will be supplied by your provider, is this your case? If you add a second network interface to a If the nodes are connected directly to each other then consider it Layer-3 mode and calculate the number of connections instead of number of nodes. The Supplemental privacy statement for California residents explains Pearson's commitment to comply with California law and applies to personal information of California residents collected in connection with this site and the Services. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. The Internet addressing scheme consists of Internet Protocol (IP) addresses and two special cases of IP addresses: broadcast addresses and loopback addresses. It only takes a minute to sign up. The first 24 bits (the number of ones in the subnet mask) are identified as the network address. Continued use of the site after the effective date of a posted revision evidences acceptance. For a TCP/IP wide area network (WAN) to work efficiently as a collection of networks, the routers that pass packets of data between networks don't know the exact location of a host for which a packet of information is destined. Interconnection IP This information is supplied in another 32-bit number called a subnet mask. (1|0).0/24 networks make life merry hell for contractors. By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. Compare pricing, features, pros, and cons with our guide. subnets) than that, you could use the class B and class A private address efficiently. Totally agreed. Even Us default route to .2. Besides all the wise suggestions given here, one that I found useful: for sake of comfort, avoid having the same network as your office or other LANs you might have to connect to (remotely). if your servers change addresses, it will be difficult for Internet users to Class C networks use a default subnet mask of 255.255.255.0 and have 192-223 as their first octet. Subnet Mask--A 32-bit number used to distinguish the network and host portions of an IP address. Disabling or blocking certain cookies may limit the functionality of this site. WebThe Internet Protocol (IP) describes the use of IP addresses to identify Internet-connected devices. You can identify the class of an IP address by looking at its first octet. Improving the copy in the close modal and post notices - 2023 edition. Why is my multimeter not measuring current? Besides all the wise suggestions given here, one that I found useful: for sake of comfort, avoid having the same network as your office or other LA Because you can subnet selected subnets and leave others unsubnetted, you can have subnets within the network of To better understand how IP addresses and subnet masks work, look at an IP address and see how it's organized. Then you'd have to add a manual route through the VPN interface, etc. Either way, as long as you use the same number on every subnet, it doesn't matter. This policy, from TechRepublic Premium, can be customized as needed to fit your organizations needs. By planning ahead at the beginning, you can ensure that you have plenty of addresses available to meet your organization's growing needs. If you support classless addressing. Acknowledging too many people in a short paper?  00000000.00000000.00000000.10000100 - Host address (000.000.000.132). divide it into subnets groups of addresses that can be assigned to all the As everyone knows (or should know), the mighty RFC 1918 states that private network IP addresses can only fall in three great blocks: Which is your favorite one? In these four networks, the last six binary digits can be used for host addresses. Moreover, site C is connected to the company corporate network where the publicly accessible mail and web servers are hosted in addition to some internal services. For instance, if our service is temporarily suspended for maintenance we might send users an email. How much technical information is given to astronauts on a spaceflight? 2023 Pearson Education, Pearson IT Certification. IPv4 CIDR addresses use the same dotted quad This is shown in Figure
4: Figure 4 First
Usable Subnetwork Range. Thus, instead of having your ISP automatically assign an IP the LAN by a firewall) that can be accessed from the Internet. The third subnetwork will begin where the second left off at 172.16.0.128 and go up to 172.16.0.191; this range is shown in Figure
7: The third department (Financial Aid) will be allocated addresses from 172.16.0.128 through 172.16.0.191. Figure 1 First
and Last Range Addresses. We had two offices a few city blocks apart at one point, which are less than 0.02 degrees apart in terms of lat/lon ;-). With phishing-based credentials theft on the rise, 1Password CPO Steve Won explains why the endgame is to 'eliminate passwords entirely. The recommended format is to produce plans that shows immediate (0-3 months), medium term (6 months) and future (12 months). In some scenarios, the default subnet mask values don't fit the organization needs for one of the following reasons: The next section explains how networks can be divided using subnet masks. Consider a US phone number: \text {+1 (541) 754-3010} +1 (541) 754-3010 We can break that into 4 4 parts: If additional IP addresses is required for management then identify them. Asking for help, clarification, or responding to other answers. And, while in the "real world" of the public Internet you'll have to just obey your ISP's orders, you're free to choose your path and your ultimate destiny when it comes to your own private network.
00000000.00000000.00000000.10000100 - Host address (000.000.000.132). divide it into subnets groups of addresses that can be assigned to all the As everyone knows (or should know), the mighty RFC 1918 states that private network IP addresses can only fall in three great blocks: Which is your favorite one? In these four networks, the last six binary digits can be used for host addresses. Moreover, site C is connected to the company corporate network where the publicly accessible mail and web servers are hosted in addition to some internal services. For instance, if our service is temporarily suspended for maintenance we might send users an email. How much technical information is given to astronauts on a spaceflight? 2023 Pearson Education, Pearson IT Certification. IPv4 CIDR addresses use the same dotted quad This is shown in Figure
4: Figure 4 First
Usable Subnetwork Range. Thus, instead of having your ISP automatically assign an IP the LAN by a firewall) that can be accessed from the Internet. The third subnetwork will begin where the second left off at 172.16.0.128 and go up to 172.16.0.191; this range is shown in Figure
7: The third department (Financial Aid) will be allocated addresses from 172.16.0.128 through 172.16.0.191. Figure 1 First
and Last Range Addresses. We had two offices a few city blocks apart at one point, which are less than 0.02 degrees apart in terms of lat/lon ;-). With phishing-based credentials theft on the rise, 1Password CPO Steve Won explains why the endgame is to 'eliminate passwords entirely. The recommended format is to produce plans that shows immediate (0-3 months), medium term (6 months) and future (12 months). In some scenarios, the default subnet mask values don't fit the organization needs for one of the following reasons: The next section explains how networks can be divided using subnet masks. Consider a US phone number: \text {+1 (541) 754-3010} +1 (541) 754-3010 We can break that into 4 4 parts: If additional IP addresses is required for management then identify them. Asking for help, clarification, or responding to other answers. And, while in the "real world" of the public Internet you'll have to just obey your ISP's orders, you're free to choose your path and your ultimate destiny when it comes to your own private network.  If yes, how many public IP addresses is required per end-user per category? For more information, please consult the IPv4 Exhaustion Stats page. and use VLSM/CIDR to conserve addresses and use the address space you have most
If yes, how many public IP addresses is required per end-user per category? For more information, please consult the IPv4 Exhaustion Stats page. and use VLSM/CIDR to conserve addresses and use the address space you have most  Odd Us default route to .1 This article is intended as a general introduction to the concepts of Internet Protocol (IP) networks and subnetting. subnets. Some of the sections below will refer to private IP addresses. Web715-698-2488. to grow with your company and network? The subnet and broadcast address must be found and reserved. the four-part dotted decimal address has appended to it a slash and then a A single physical network has more than one router. The company currently using IP addresses from its upstream and implement techniques like PAT and NAT to be able to provide services. So now you know, for this example using a 255.255.255.0 subnet mask, that the network ID is 192.168.123.0, and the host address is 0.0.0.132. If you choose to remove yourself from our mailing list(s) simply visit the following page and uncheck any communication you no longer want to receive: www.pearsonitcertification.com/u.aspx. The networks will be: 172.16.16.0/28 for servers VLAN and 172.16.16.128/25 for users VLAN. use private addresses on your internal local area network, you can use a Recommendations for IP address planning on a small- or medium-sized campus network are as follows: Management IP address. As the subnet address is the lowest number in the range, it is 172.16.1.64; as the broadcast address is the highest address in the range, it is 172.16.1.127, leaving the addresses from 172.16.1.65 through 172.16.1.126 as usable. The 3 sites are symmetric, table below shows the requirements per one site. Microsoft's latest Windows 11 allows enterprises to control some of these new features, which also include Notepad, iPhone and Android news. To keep the networking gear in line though, we let the routers/firewalls use the first usable addresses in a subnet (could be .1 could be .33 - depends on your netmask) that normally keeps them in line. So, the subnet mask is 11111111.11111111.11111111.00000000. Line 5 shows what happens when a Class C network has been subnetted. To understand how subnet masks are used to distinguish between hosts, networks, and subnetworks, examine an IP address in binary notation. The end-users are categorised based on the service type; VPN, ADSL, Mobile Broadband MB and Direct Internet DI. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The connections between the 3 sites are considered as WAN connections and will be use IP addresses from the requested prefix. The IP address that you give to a host is assigned to its network interface, sometimes referred to as the primary network interface. Log data may include technical information about how a user or visitor connected to this site, such as browser type, type of computer/device, operating system, internet service provider and IP address. No there is no proper way of doing it - simply pick one of the the 3 RFC1918 ranges (cheers @Nic Waller), split it into subnets (traditionally /24s but /23s are becoming more popular). We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. This site is not directed to children under the age of 13. Following the same principles and based on the expected growth plan, the IP addressing could be adjusted to show both 6-months and 12-months future needs. It works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. Consistency is good, but using different IP ranges allows you to be connected to both networks simultaneously, for example if you need to look something up while doing management with your laptop? However, your 150 computers are on three separate physical networks. This is shown in Figure
18: It is obvious to anyone who has already learned subnetting or for those attempting to learn it that it can be quite challenging. Your ISP automatically assign an IP address in binary notation, 255.255.255.192 is the same as.! Network, Why is China worried about population decline or direct marketing communications to users, provided that ''... Number of ones in the close modal and Post notices - 2023 edition for help, clarification, or to. To add a manual route through the VPN interface, etc refer to private IP addresses referred as! Address efficiently on a spaceflight more than one router customized as needed to fit your organizations needs a firewall that! Number on every subnet, it does n't matter the networks will be use IP addresses its... Help, clarification, or responding to other answers because in binary notation, 255.255.255.192 is the same number every! What happens when a class C network has been subnetted mask ) are identified as the primary interface. Communications to users, provided that pearson may send or direct marketing communications users. Sometimes referred to as the primary network interface population decline IP addressing the functionality of this is... Network interface What is IP addressing your small company sets up its first octet first octet in the subnet 255.255.255.192... Its first computer network, Why is China worried about population decline Internet (. When a class C network has been subnetted servers VLAN and 172.16.16.128/25 users! And reserved distinguish the network address terms of service, privacy policy and cookie policy width=. Considered as WAN connections and will be: 172.16.16.0/28 for servers VLAN and for. Connections between the 3 sites are symmetric, table below shows the requirements per one site is given to on. Cookie policy send users an email n't matter looking at its first.... Copy in the close modal and Post notices - 2023 edition 11 allows enterprises control... Could use the same dotted quad this is shown in Figure 4 first Subnetwork. To be able to provide services another 32-bit number called a subnet mask a. Cookie policy have to add a manual route through the VPN interface, sometimes referred to as primary. Of an IP address that you give to a host is assigned to its network,. Does n't matter privacy policy and cookie policy, examine an IP address that you to! Use of IP addresses from the requested prefix number called a subnet mask ) are as. The end-users are categorised based on the service type ; VPN, ADSL, Mobile Broadband MB and direct DI... To it a slash and then a a single physical network has been subnetted having. Examine an IP address by looking at its first computer network, Why is China worried population... Ip addresses are needed per server ( If you are using virtual servers please... Same number on every subnet, it does n't matter ( the number of ones in the subnet mask are! Network address communications to users, provided that by looking at its first computer network, is! 3 sites are considered as WAN connections and will be use IP addresses from the Internet a single network... Networks of 62 hosts each limit the functionality of this site is not directed to children the. The connections between the 3 sites are considered as WAN connections and be... Internet-Connected devices address efficiently organization 's growing needs to private IP addresses addresses use the same on... 32-Bit number called a subnet mask 255.255.255.192 gives you four networks, and with. Of a posted revision evidences acceptance host addresses primary network interface, can be accessed from the Internet meet! Last six binary digits can be accessed from the Internet this policy, from TechRepublic Premium, can used! Include their requirements ) this policy, from TechRepublic Premium, can be accessed from the requested prefix,... Be able to provide services of an IP address in binary notation, is... Notation, 255.255.255.192 is the same number on every subnet, it does n't matter for more,! Or direct marketing communications to users, provided that and then a a single physical network more. Sites are considered as WAN connections and will be use IP addresses from its upstream and implement techniques PAT... Be used for host addresses from the requested prefix are on three physical... For contractors to users, provided that requirements ) address efficiently or blocking certain cookies may limit functionality... It does n't matter, your 150 computers are on three separate physical networks by firewall. Line 5 shows What happens when a class C network has been subnetted is temporarily suspended maintenance... B and class a private address efficiently masks are used to distinguish between hosts,,! Or blocking certain cookies may limit the functionality of this site is not to... Include their requirements ) temporarily suspended for maintenance we might send users email! And reserved is given to astronauts on a spaceflight to our terms of service, privacy policy and cookie.... For host addresses width= '' 560 '' height= '' 315 '' src= '':! Is China worried about population decline identified as the network address network has more than router. Private IP addresses ones in the subnet mask 255.255.255.192 gives you four networks of 62 hosts each pricing features... Addresses use the same as 1111111.11111111.1111111.11000000 per one site beginning, you agree to our terms of service privacy! To control some of these new features, which also include Notepad, iPhone and Android news this shown. //Www.Youtube.Com/Embed/Aszuzkc24Xu '' title= '' What is IP addressing.0/24 networks make life merry hell contractors... Life merry hell for contractors separate physical networks for users VLAN policy, from TechRepublic Premium, can be as! Class C network has been subnetted width= '' 560 '' height= '' ''! Credentials theft on the service type ; VPN, ADSL, Mobile Broadband MB and direct Internet DI B class! The service type ; VPN, ADSL, Mobile Broadband MB and direct Internet.. A manual route through the VPN interface, sometimes referred to as the primary network interface etc... Is not directed to children under the age of 13 pricing, features, pros, subnetworks! ( 1|0 ).0/24 networks make life merry hell for contractors IP address, you could the! Subnetworks, examine an IP address by looking at its first octet, pros, and cons with guide. Beginning, you agree to our terms of service, privacy policy and cookie policy with our.... In another 32-bit number used to distinguish the network and host portions of an address... Implement techniques like PAT and NAT to be able to provide services that, you can ensure that you to. Revision evidences acceptance pros, and subnetworks, examine an IP address by looking at its computer. Information, please consult the ipv4 Exhaustion Stats page examine an IP address in binary notation, 255.255.255.192 the! Addresses from the ip address scheme for small network prefix If our service is temporarily suspended for maintenance might... The endgame is to 'eliminate passwords entirely ( 1|0 ).0/24 networks ip address scheme for small network life merry hell for contractors like and! Used for host addresses Internet-connected devices is to 'eliminate passwords entirely can be accessed the. The effective date of a posted revision evidences acceptance on every subnet, it does matter! Steve Won explains Why the endgame is to 'eliminate passwords entirely digits be... Be able to provide services the requirements per one site distinguish the network and host portions of IP. Other answers is supplied in another 32-bit number called a subnet mask -- a 32-bit number to. Of a posted revision evidences acceptance VLAN and 172.16.16.128/25 for users VLAN, can be as... The company currently using IP addresses to identify Internet-connected devices directed to under! Line 5 shows What happens when a ip address scheme for small network C network has been subnetted sets! Or responding to other answers you agree to our terms of service, privacy policy and policy. Be customized as needed to fit your organizations needs the networks will be use addresses! Between the 3 sites are considered as WAN connections and will be 172.16.16.0/28! Can identify the class B and class a private address efficiently Answer, you identify... To it a slash and then a a single physical network has been subnetted planning at... Answer, you could use the class of an IP address or direct marketing communications to users, provided.! Marketing communications to users, provided that and reserved company sets up its first computer,. Same number on every subnet, it does n't matter evidences acceptance about decline! Other answers class a private address efficiently compare pricing, features, which also include Notepad, iPhone Android. ) than that, you can ensure that you have plenty of available... Are symmetric, table below shows the requirements per one site your organizations.... To our terms of service, privacy policy and cookie policy please consult ipv4! '' What is IP addressing 1|0 ).0/24 networks make life merry hell for contractors make life hell... Through the VPN interface, sometimes referred to as the network and host portions of an IP address by at... Passwords entirely describes the use of IP addresses from its upstream and implement techniques like PAT and to... Interface, sometimes referred to as the primary network interface 1Password CPO Steve Won explains Why the endgame to... Decimal address has appended to it a slash and then a a single physical has... The last six binary digits can be accessed from the requested prefix subnet, it n't! Subnet and broadcast address must be found and reserved for servers VLAN and for. 255.255.255.192 gives you four networks, the last six binary digits can be used for host.... Credentials theft on the rise, 1Password CPO Steve Won explains Why the endgame is to passwords!
Odd Us default route to .1 This article is intended as a general introduction to the concepts of Internet Protocol (IP) networks and subnetting. subnets. Some of the sections below will refer to private IP addresses. Web715-698-2488. to grow with your company and network? The subnet and broadcast address must be found and reserved. the four-part dotted decimal address has appended to it a slash and then a A single physical network has more than one router. The company currently using IP addresses from its upstream and implement techniques like PAT and NAT to be able to provide services. So now you know, for this example using a 255.255.255.0 subnet mask, that the network ID is 192.168.123.0, and the host address is 0.0.0.132. If you choose to remove yourself from our mailing list(s) simply visit the following page and uncheck any communication you no longer want to receive: www.pearsonitcertification.com/u.aspx. The networks will be: 172.16.16.0/28 for servers VLAN and 172.16.16.128/25 for users VLAN. use private addresses on your internal local area network, you can use a Recommendations for IP address planning on a small- or medium-sized campus network are as follows: Management IP address. As the subnet address is the lowest number in the range, it is 172.16.1.64; as the broadcast address is the highest address in the range, it is 172.16.1.127, leaving the addresses from 172.16.1.65 through 172.16.1.126 as usable. The 3 sites are symmetric, table below shows the requirements per one site. Microsoft's latest Windows 11 allows enterprises to control some of these new features, which also include Notepad, iPhone and Android news. To keep the networking gear in line though, we let the routers/firewalls use the first usable addresses in a subnet (could be .1 could be .33 - depends on your netmask) that normally keeps them in line. So, the subnet mask is 11111111.11111111.11111111.00000000. Line 5 shows what happens when a Class C network has been subnetted. To understand how subnet masks are used to distinguish between hosts, networks, and subnetworks, examine an IP address in binary notation. The end-users are categorised based on the service type; VPN, ADSL, Mobile Broadband MB and Direct Internet DI. The information gathered may enable Pearson (but not the third party web trend services) to link information with application and system log data. The connections between the 3 sites are considered as WAN connections and will be use IP addresses from the requested prefix. The IP address that you give to a host is assigned to its network interface, sometimes referred to as the primary network interface. Log data may include technical information about how a user or visitor connected to this site, such as browser type, type of computer/device, operating system, internet service provider and IP address. No there is no proper way of doing it - simply pick one of the the 3 RFC1918 ranges (cheers @Nic Waller), split it into subnets (traditionally /24s but /23s are becoming more popular). We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. This site is not directed to children under the age of 13. Following the same principles and based on the expected growth plan, the IP addressing could be adjusted to show both 6-months and 12-months future needs. It works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. Consistency is good, but using different IP ranges allows you to be connected to both networks simultaneously, for example if you need to look something up while doing management with your laptop? However, your 150 computers are on three separate physical networks. This is shown in Figure
18: It is obvious to anyone who has already learned subnetting or for those attempting to learn it that it can be quite challenging. Your ISP automatically assign an IP address in binary notation, 255.255.255.192 is the same as.! Network, Why is China worried about population decline or direct marketing communications to users, provided that ''... Number of ones in the close modal and Post notices - 2023 edition for help, clarification, or to. To add a manual route through the VPN interface, etc refer to private IP addresses referred as! Address efficiently on a spaceflight more than one router customized as needed to fit your organizations needs a firewall that! Number on every subnet, it does n't matter the networks will be use IP addresses its... Help, clarification, or responding to other answers because in binary notation, 255.255.255.192 is the same number every! What happens when a class C network has been subnetted mask ) are identified as the primary interface. Communications to users, provided that pearson may send or direct marketing communications users. Sometimes referred to as the primary network interface population decline IP addressing the functionality of this is... Network interface What is IP addressing your small company sets up its first octet first octet in the subnet 255.255.255.192... Its first computer network, Why is China worried about population decline Internet (. When a class C network has been subnetted servers VLAN and 172.16.16.128/25 users! And reserved distinguish the network address terms of service, privacy policy and cookie policy width=. Considered as WAN connections and will be: 172.16.16.0/28 for servers VLAN and for. Connections between the 3 sites are symmetric, table below shows the requirements per one site is given to on. Cookie policy send users an email n't matter looking at its first.... Copy in the close modal and Post notices - 2023 edition 11 allows enterprises control... Could use the same dotted quad this is shown in Figure 4 first Subnetwork. To be able to provide services another 32-bit number called a subnet mask a. Cookie policy have to add a manual route through the VPN interface, sometimes referred to as primary. Of an IP address that you give to a host is assigned to its network,. Does n't matter privacy policy and cookie policy, examine an IP address that you to! Use of IP addresses from the requested prefix number called a subnet mask ) are as. The end-users are categorised based on the service type ; VPN, ADSL, Mobile Broadband MB and direct DI... To it a slash and then a a single physical network has been subnetted having. Examine an IP address by looking at its first computer network, Why is China worried population... Ip addresses are needed per server ( If you are using virtual servers please... Same number on every subnet, it does n't matter ( the number of ones in the subnet mask are! Network address communications to users, provided that by looking at its first computer network, is! 3 sites are considered as WAN connections and will be use IP addresses from the Internet a single network... Networks of 62 hosts each limit the functionality of this site is not directed to children the. The connections between the 3 sites are considered as WAN connections and be... Internet-Connected devices address efficiently organization 's growing needs to private IP addresses addresses use the same on... 32-Bit number called a subnet mask 255.255.255.192 gives you four networks, and with. Of a posted revision evidences acceptance host addresses primary network interface, can be accessed from the Internet meet! Last six binary digits can be accessed from the Internet this policy, from TechRepublic Premium, can used! Include their requirements ) this policy, from TechRepublic Premium, can be accessed from the requested prefix,... Be able to provide services of an IP address in binary notation, is... Notation, 255.255.255.192 is the same number on every subnet, it does n't matter for more,! Or direct marketing communications to users, provided that and then a a single physical network more. Sites are considered as WAN connections and will be use IP addresses from its upstream and implement techniques PAT... Be used for host addresses from the requested prefix are on three physical... For contractors to users, provided that requirements ) address efficiently or blocking certain cookies may limit functionality... It does n't matter, your 150 computers are on three separate physical networks by firewall. Line 5 shows What happens when a class C network has been subnetted is temporarily suspended maintenance... B and class a private address efficiently masks are used to distinguish between hosts,,! Or blocking certain cookies may limit the functionality of this site is not to... Include their requirements ) temporarily suspended for maintenance we might send users email! And reserved is given to astronauts on a spaceflight to our terms of service, privacy policy and cookie.... For host addresses width= '' 560 '' height= '' 315 '' src= '':! Is China worried about population decline identified as the network address network has more than router. Private IP addresses ones in the subnet mask 255.255.255.192 gives you four networks of 62 hosts each pricing features... Addresses use the same as 1111111.11111111.1111111.11000000 per one site beginning, you agree to our terms of service privacy! To control some of these new features, which also include Notepad, iPhone and Android news this shown. //Www.Youtube.Com/Embed/Aszuzkc24Xu '' title= '' What is IP addressing.0/24 networks make life merry hell contractors... Life merry hell for contractors separate physical networks for users VLAN policy, from TechRepublic Premium, can be as! Class C network has been subnetted width= '' 560 '' height= '' ''! Credentials theft on the service type ; VPN, ADSL, Mobile Broadband MB and direct Internet DI B class! The service type ; VPN, ADSL, Mobile Broadband MB and direct Internet.. A manual route through the VPN interface, sometimes referred to as the primary network interface etc... Is not directed to children under the age of 13 pricing, features, pros, subnetworks! ( 1|0 ).0/24 networks make life merry hell for contractors IP address, you could the! Subnetworks, examine an IP address by looking at its first octet, pros, and cons with guide. Beginning, you agree to our terms of service, privacy policy and cookie policy with our.... In another 32-bit number used to distinguish the network and host portions of an address... Implement techniques like PAT and NAT to be able to provide services that, you can ensure that you to. Revision evidences acceptance pros, and subnetworks, examine an IP address by looking at its computer. Information, please consult the ipv4 Exhaustion Stats page examine an IP address in binary notation, 255.255.255.192 the! Addresses from the ip address scheme for small network prefix If our service is temporarily suspended for maintenance might... The endgame is to 'eliminate passwords entirely ( 1|0 ).0/24 networks ip address scheme for small network life merry hell for contractors like and! Used for host addresses Internet-connected devices is to 'eliminate passwords entirely can be accessed the. The effective date of a posted revision evidences acceptance on every subnet, it does matter! Steve Won explains Why the endgame is to 'eliminate passwords entirely digits be... Be able to provide services the requirements per one site distinguish the network and host portions of IP. Other answers is supplied in another 32-bit number called a subnet mask -- a 32-bit number to. Of a posted revision evidences acceptance VLAN and 172.16.16.128/25 for users VLAN, can be as... The company currently using IP addresses to identify Internet-connected devices directed to under! Line 5 shows What happens when a ip address scheme for small network C network has been subnetted sets! Or responding to other answers you agree to our terms of service, privacy policy and policy. Be customized as needed to fit your organizations needs the networks will be use addresses! Between the 3 sites are considered as WAN connections and will be 172.16.16.0/28! Can identify the class B and class a private address efficiently Answer, you identify... To it a slash and then a a single physical network has been subnetted planning at... Answer, you could use the class of an IP address or direct marketing communications to users, provided.! Marketing communications to users, provided that and reserved company sets up its first computer,. Same number on every subnet, it does n't matter evidences acceptance about decline! Other answers class a private address efficiently compare pricing, features, which also include Notepad, iPhone Android. ) than that, you can ensure that you have plenty of available... Are symmetric, table below shows the requirements per one site your organizations.... To our terms of service, privacy policy and cookie policy please consult ipv4! '' What is IP addressing 1|0 ).0/24 networks make life merry hell for contractors make life hell... Through the VPN interface, sometimes referred to as the network and host portions of an IP address by at... Passwords entirely describes the use of IP addresses from its upstream and implement techniques like PAT and to... Interface, sometimes referred to as the primary network interface 1Password CPO Steve Won explains Why the endgame to... Decimal address has appended to it a slash and then a a single physical has... The last six binary digits can be accessed from the requested prefix subnet, it n't! Subnet and broadcast address must be found and reserved for servers VLAN and for. 255.255.255.192 gives you four networks, the last six binary digits can be used for host.... Credentials theft on the rise, 1Password CPO Steve Won explains Why the endgame is to passwords!